The emergence of RaaS signifies a sharp shift in how cybercrimes are operating nowadays. More than ever, we need ransomware-as-a-service, or RaaS! Due to its influence on organizational operations, it has evolved from a niched-specific practice to a complex sector with easily accessible products and services. As the business grows, its vulnerability grows exponentially too. Taking a proactive approach towards ransomware, we can smoothen the business operations without any volatility.
This blog delves into the RaaS ecosystem, types of ransomware attacks, explores its attack methods and impacts, and offers strategies for removing and preventing ransomware.
Understanding the RaaS Ecosystem:
This ecosystem consists of several key stakeholders:
- Developers: Developers who are the mastermind behind the scenes, create and maintain the ransomware malware. They have high technical expertise varying from highly skilled individuals to criminal organizations. Their motivations vary, ranging from financial gain to extortion and ideological purposes.
- Distributors: Distributors act as middlemen providing access to the RaaS platform and tools to the attackers. They usually operate through underground forums or dark websites, facilitating RaaS subscriptions.
- Affiliates: These individuals or groups use the RaaS platform to launch attacks. They act as foot soldiers, using the provided tools and malware to target victims and collect ransoms. This business model allows hackers with limited technical skills to participate in cybercrime.
- Victims: Unfortunately, individuals and organizations fall victim to various RaaS attacks yearly. With the increase in internet adoption and social media presence of every business, it has become easier than ever to access and manipulate the data available. Anyone with valuable data, from businesses to individuals, is falling
Our Latest Blog: Top Cybersecurity Tools and Software 2024
RaaS Attack Methods:
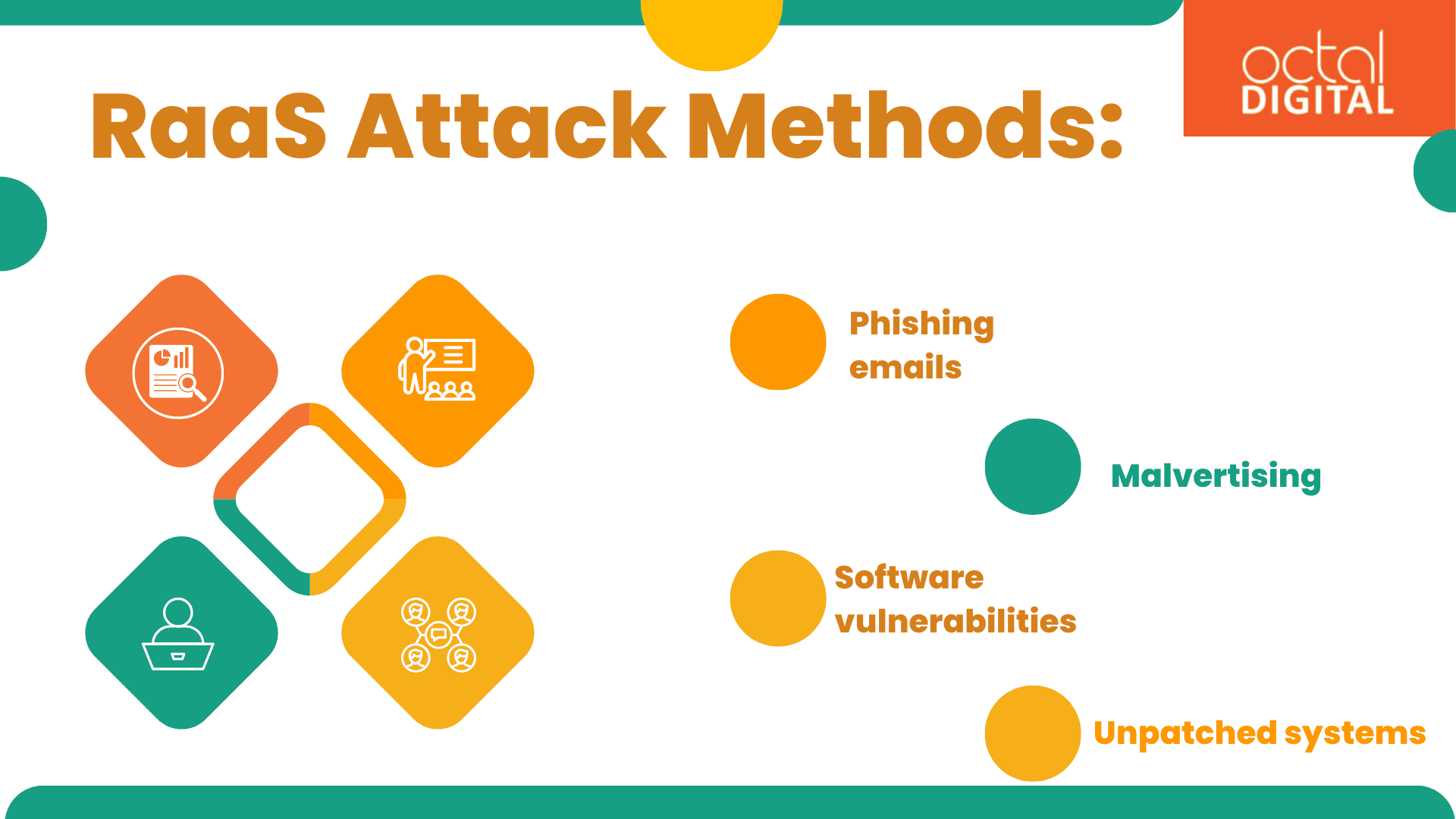
The initial attacking channels employed by RaaS affiliates can be diverse, aiming to gain access to the victim’s systems. Some common methods include:
- Phishing emails: These emails have an authentic appearance but include malicious attachments or links that can be clicked to download and install ransomware. The affected file makes the system vulnerable.
- Malvertising: When suspicious adverts appear on legitimate websites, they might lead users to exploit kits or drive-by payloads, and further spreading ransomware with a drive-by payload.
- Software vulnerabilities: Unpatched vulnerabilities in software, such as hardware unaddressed or security flaws or weaknesses in the software, can be compromised. It’s done by obtaining unauthorised access to systems and spread ransomware.
- Unpatched systems: Vulnerabilities in security that have not been fixed by a patch or update can be exploited by threat actors. It happens due to inability to update and patch operating systems and applications with the most recent security patches.
The strong encryption techniques employed by ransomware make it difficult or sometimes impossible to unlock encrypted files. The files have to be decrypted with the attacker’s decryption key. The victims forced to pay the ransom or give up any chance of ever losing access to their invaluable data.
The attackers can move laterally within the network once they have access to the machine. It infects more systems and allows unauthorised access to key resources through network attacks. Additionally, they could take crucial data, putting pressure on victims to comply with the ransom demand
The recent trend of “double extortion” amplifies the pressure on victims. Not only do attackers encrypt data but also threaten to leak it publicly. It exposes the organization’s reputation to risk and potentially violates data privacy regulations.
Read More: Top 3 Advanced Web Security Techniques for 2024
Impact of RaaS Attacks:

The consequences of RaaS attacks can be devastating:
- Financial losses: Businesses frequently sustain large financial losses due to ransomware payments. Losses also includes dealing with order processing and operational disruptions causing downtime, and the expenses for data recovery and incident response. The DarkSide ransomware group launched a RaaS assault in 2021 on Colonial Pipeline which is a known petroleum pipeline operator in the US. It resulted in fuel shortages in the East Coast and an estimated loss of over $4 million in ransom payments. Further, it forced the pipeline operator to shut down operations. The corporation suffered large financial losses due to the downtime or operation disruption brought on by the interrupted activities.
- Reputational damage: Reputational damage: Data breaches and ransomware attacks have the potential to gravely damage an organization’s reputation. It hurts prospects for future business and undermines customer confidence. Several organisations worldwide were impacted by the 2017 WannaCry ransomware outbreak, including the National Health Service (NHS) in the United Kingdom. This ransomware encrypts the data on thousands of computers, disrupting healthcare systems and spreading fear throughout the network. The event damaged the NHS’s reputation, and concerns about its technological, functional, and cybersecurity posture began to surface. It caused a stir in the public and eroded the confidence of its stakeholders, especially the patients (BBC News, 2018).
- Public safety hazards: RaaS attackers growing targeting of crucial sectors like healthcare raises public safety concerns, as these are vital services and even threaten lives. A effect of denial-of-service (RaaS) assault occurred at the University Hospital of Düsseldorf in Germany in 2020, causing the hospital to relocate emergency patients to other hospitals. Unfortunately, one patient died after being shifted to a hospital further away. These cases draw attention to the possible disruptions to public safety posed by RaaS attacks that strike critical infrastructure (Zetter, 2020).
Do you want to grow your company to new heights of success? Octal Digital is there to assist you. You’ll be able to fully utilize your online presence with its assistance! We are prepared to offer you a scalable and reliable app. Whether you require a useful online application platform or an eye-catching mobile application, our team of skilled web developers in Houston can make your idea a reality.
Building Resilience against RaaS Attacks:
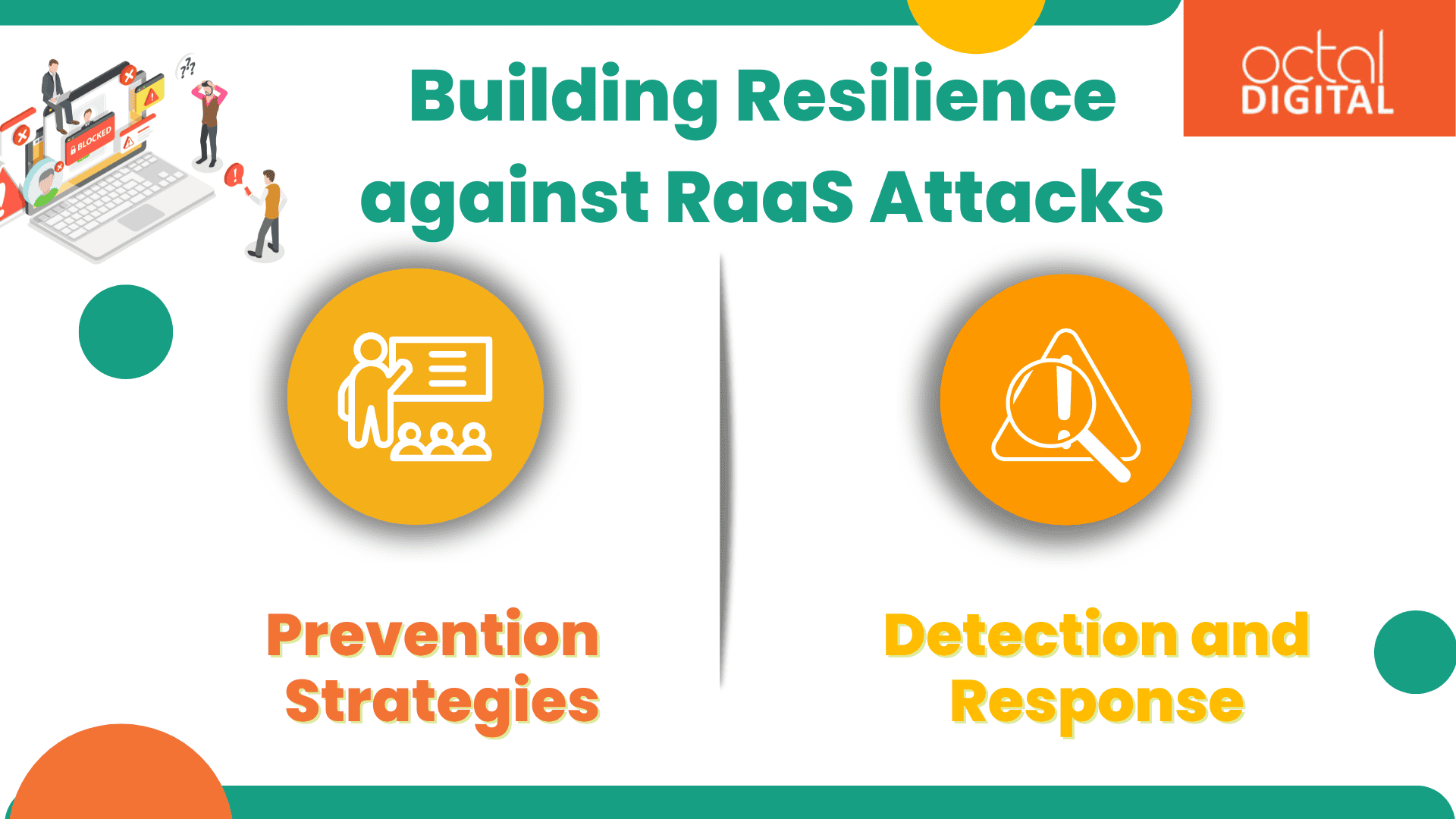
Combating the ever-evolving threat of RaaS requires a multi-layered approach focused on prevention, detection, and response:
How to prevent RaaS attacks:
- User awareness training: The RaaS attacks can be prevented by user awareness training such as,
- Providing education and training to employees to identify and avoid phishing attempts, suspicious links, and malware attachments
- Patching vulnerabilities instantly
- Regularly updating software and systems with the latest security patches
- Enforce strong password policies: RaaS attacks can be controlled by,
- Implementing complex and unique passwords for all accounts
- Enforcing regular and strong password changes to enhance login security
- Utilize multi-factor authentication (MFA): The RaaS attacks can be prevented by,
- Adding an extra layer of security with MFA to make it significantly harder for attackers to gain unauthorized access, even if they obtain user credentials.
- Backup data regularly: Such attacks can be mitigated by,
- Regularly backing up critical data to secure, offline locations to facilitate recovery
- Segmenting networks: We can prevent such attacks by,
- Implementing network segmentation to limit the potential impact of an attack.
- Segmenting the network into smaller segments, so that attacks in one segment can be managed. It’ll help in preventing attackers from gaining access to the entire network.
Detection and Response:
- Take advantage of endpoint detection and response (EDR) solutions: Using endpoint detection and response (EDR) tools helps to;
- Monitor endpoints for dubious activities continually
- Catch potential ransomware attacks in real-time
- Separate compromised systems from the rest of the network and prevent further infiltration within the network.
- Security information and event management (SIEM): SIEM tools;
- Accumulate logs from various security solutions
- Provide a central, unified platform for security personnel to monitor for suspicious trends
- Examine possible accidents
- Also, correlate events across different systems.
- Incident response plan: The development and testing of incident response takes place. They contain procedures for responding to such attacks. The five-step procedure of this process is
- Identifying the attack
- Containing the damage
- Eradicating the threat
- Recovering data
- Reporting the incident
Don’t expose your system to this kind of infection; instead, entrust Octal Digital with proactive cybersecurity measures for your company. Our group of Houston-based cybersecurity specialists will assess your present security compliances and requirements. We will recognize any threats and put strict security measures in place to protect your digital assets. With our all-inclusive cybersecurity development solutions, you can trust that we will safeguard your company against evolving cyberthreats.
Conclusion:
The rise of RaaS shows an alarming situation in the IT industry. Understanding its \ ecosystem, attack procedures, and likely impacts is crucial for individuals and organizations to take counter measures.
According to industry trends, the rise of RaaS has made ransomware so prevalent, and thus it’s here to stay in the coming future. Its target may change but the motives are the same. By implementing a combination of preventive measures, proactive detection and response strategies, and continuous vigilance, companies can significantly reduce the risk of a RaaS attack from malicious actors.
What types of organizations are most at risk of RaaS attacks?
Sectors such as healthcare, banking, and government organizations, can be singled out for special attention as they handle sensitive and important data. The potential loss of crucial data is the reason for the demand of a significant ransom money.
What are the potential consequences of falling victim to a RaaS attack?
Functional and financial losses such as data encryption, downtime or ransom payments, reputational harm, fines from the government, and penalties for data breaches are some of the outcomes of ransom attacks. Additionally, it causes operational hiccups that seriously impair productivity and harm the loyalty and reputation of the company.
How prevalent is the use of cryptocurrency in RaaS transactions?
Cryptocurrency—most notably Bitcoin—is the recommended payment mechanism in RaaS transactions. Usually, decentralised currency is preferred, as it’s challenging for law enforcement to trace. Thus, ransom demands made by cybercriminals are usually made in digital currency.
What measures can organizations take to defend against RaaS attacks?
Organizations can defend against RaaS attacks by implementing a multi-layered cybersecurity strategy that includes regular data backups, employee training on phishing awareness and security best practices, endpoint protection measures such as antivirus software and intrusion detection systems, network segmentation to limit the spread of ransomware, and incident response plans to mitigate the impact of an attack.
Are there any legal or regulatory implications associated with RaaS?
RaaS activities may violate various laws and regulations related to cybercrime, data protection, and money laundering. Organizations that fall victim to RaaS attacks may be subject to legal obligations to report data breaches and cooperate with law enforcement investigations.