The digital world is continuously innovating and growing especially cloud services offering numerous opportunities for the users. But so does the malicious attacks and cybersecurity threats. Cybersecurity plays a crucial role in protecting and securing databases, tools, user’s data and software.
It uses tools and approaches to safeguard individuals and organizations from various cyber threats. Such tools provide various functions, such as network security, endpoint security, encryption, and identity management. Cybersecurity tools help the users and organizations because it enables your company make informed decisions regarding building a robust defence against cyberattacks.
To get a comprehensive overview of various cybersecurity tools in this blog, keep reading this blog. Such software are categorized by respective functions, benefits, drawbacks, and examples to make sense of cybersecurity.
Understanding Your Requirements for Cybersecurity Tools

Before considering cybersecurity, first consider the requirements you face. Without planning out your needs and requirements, choosing a good cybersecurity tool is impossible. Key factors to consider are:
- Size and Nature: Different needs arise according to your company’s scalability and complexity. For example, size and nature differ for a start-up, SME’s and large enterprises, and thus, the security requirements changes.
- Data Sensitivity: Financial information, personally identifiable information (PII), intellectual property, and other sensitive data necessitate stronger security measures. Choose what type of data your company deals in and need to protect.
- Vulnerability Landscape:Are you vulnerable to some specific threats because of your industry/niche? Common threats in this landscape may include malware, phishing emails, ransom ware attacks, and unauthorized access attempts. For example, a crypto based company is more prone to threats than other industry segments.
- Budget and Resources:Always consider your budget and the technical expertise of your employees within your organization to manage and maintain these tools post launch.
#TLDR: A Quick Reference Table for Cybersecurity Tools
This table will help you to choose right cybersecurity tools for your business, based on specific requirements:
| Category | Description | Example Cybersecurity Tools | Benefits | Drawbacks |
| Network Security | Protect networks from unauthorized access and malicious activity | – Firewalls (Windows Firewall, pfSense) | – Blocks malicious traffic | – Can be complex to configure |
| – Intrusion Detection/Prevention Systems (Snort, Security Onion) | – Detects and/or prevents suspicious network activity | – May generate false positives | ||
| – Vulnerability Scanners (Nessus, OpenVAS) | – Identifies weaknesses in systems and applications | – Requires ongoing maintenance | ||
| – Network Traffic Analysis (Zeek, ELK Stack) | – Analyzes network traffic patterns for anomalies | – Requires expertise to interpret data | ||
| Endpoint Security | Protect devices from malware and other threats | – Antivirus/Anti-malware (McAfee, Norton) | – Scans for and removes malicious software | – May not detect all threats |
| – Endpoint Detection and Response (Crowdstrike Falcon, SentinelOne) | – Detects, investigates, and responds to endpoint threats | – Can be expensive | ||
| – Application Control/Whitelisting (AppLocker, Microsoft Defender Application Control) | – Restricts users from running unauthorized applications | – May require user training | ||
| Encryption & Data Security | Encrypt data for secure storage and transmission | – Data encryption software (VeraCrypt, PGP) | – Protects data confidentiality | – Can be complex to manage |
| – Data Loss Prevention (DLP) (McAfee DLP, Microsoft Endpoint Data Loss Prevention) | – Monitors and controls data movement to prevent leaks | – Can impact user productivity | ||
| Identity & Access Management (IAM) | Manage user identities, access controls, and permissions | – Multi-factor authentication (MFA) | – Adds an extra layer of security beyond passwords | – May require additional user steps |
| – Single Sign-On (SSO) (Microsoft Azure AD, Okta) | – Allows single login for multiple apps | – Requires integration with various applications | ||
| – Identity and Access Management (IAM) platforms (SailPoint, Azure Active Directory) | – Centralized platform for managing user identities and access | – Can be complex to implement and manage | ||
| Security Information and Event Management (SIEM) | Aggregate and analyze logs from various security tools | – Splunk, LogRhythm | – Provides centralized view of security events | – Requires expertise to configure and interpret data |
Read More: Blockchain Security Challenges and Opportunities 2024
Types of Cybersecurity Tools and Software:
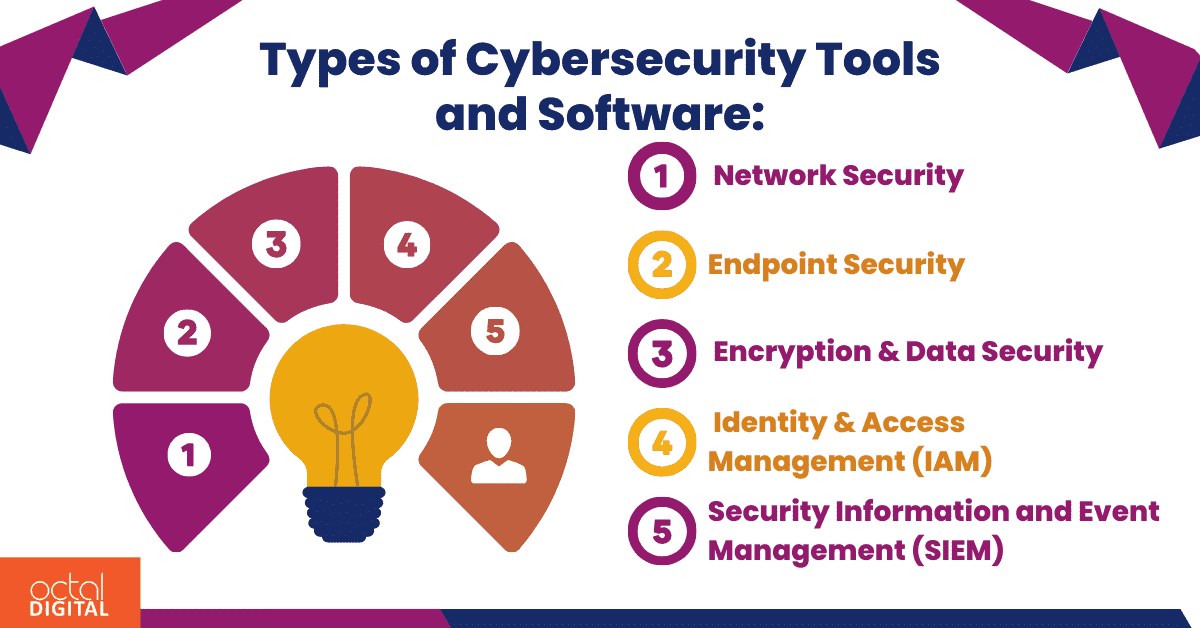
Now when you have understood your needs, now comes the selection part in which you have to choose between diverse range of cybersecurity tools and software available:
#1 Cybersecurity Tools: Network Security:
- Firewalls: Cybersecurity tools act as the initial defence. It filters all incoming and outgoing network traffic as already defined by security rules. The tools can block malicious traffic while allowing safe traffic to pass through. Examples of popular firewall cybersecurity tools options include Windows Firewall (built-in with Windows OS), pfSense (open-source firewall solution), and various commercial firewalls offered by security vendors.
- Intrusion Detection/Prevention Systems (IDS/IPS): These continuously monitors Network traffic is for suspicious activities. These activities constantly that indicate an for all attempted attack and alerts security staff while simultaneously blocking them. Some of the popular tools include Snort (open-source IDS), Security Onion (open-source security platform), or commercial solutions from Palo Alto Networks and Cisco .
Octal Digital offers secure development solutions to minimize potential risks before they can impact your business. Using cutting-edge technologies and industry best practices, Octal Digital implements a proactive cyber strategy. It includes continual monitoring, analyzing threat intelligence, and rapid response systems protocol. Our team of cybersecurity experts try to keep pace with emerging threats. We keep check on evolving attack vectors so that your organization proactively manage cyber threats. Don’t wait until it’s too late – contact Octal Digital today to defend your business and protect your business from cyber threats.
- Vulnerability Scanners: These are programmes that check your apps and systems for security holes. Preventing successful attacks requires first identifying those threats and then resolving them. Some examples are Qualys Vulnerability Management Platform (a commercial solution), OpenVAS (an open-source scanner), and Nessus (a commercial scanner with a free community edition).
- Network traffic analysis (NTA) tools: These cybersecurity instruments examine patterns of network traffic in order to spot irregularities and possible dangers. With the aid of these tools, you can identify odd behaviour patterns, dubious connections, and possible malware infestations. These tools include the open-source Zeek platform, the commercial Darktrace solution, and the open-source ELK Stack log analysis platform.
#2 Cybersecurity Tools: Endpoint Security:
- Antivirus/Anti-malware software:They are very commonly used for protecting devices from malware threats such as spyware, and ransom ware. They scan downloaded files, system files, etc for malicious code. They take various actions like removing those threats after identifying them. McAfee, Norton, Bitdefender, and Windows Defender (built-in with Windows OS) are some popular antiviruses.
- Endpoint Detection and Response (EDR) tools:EDR tools alert security teams of any uncommon, malicious activity. They enable quick investigation and solution of attacks on endpoints. An endpoint means an employee workstation or laptop, a server, a cloud system, a mobile or IoT device. Crowdstrike Falcon, SentinelOne, and Microsoft Defender for Endpoint (EDR capabilities included in the commercial offering) are included in this type.
- Application Control/Whitelisting:They restricts the usage of any blocked/blacklisted tools or applications in background and only allow those that are approved. Organizations do this by employing a system administrator or third-party app to manage the list of apps. Then they enforce these restrictions. AppLocker (built-in with Windows OS), Application Whitelisting for Microsoft Defender Antivirus, are some go-to endpoint security solutions with application control features.
#3 Cybersecurity Tools: Encryption & Data Security:
- Data encryption software: Encryption is a building block in cyber security. In this data is entered into an encoded format so that no unauthorized person has access to it. It is useful for protecting sensitive data while storage and while being transferred between devices or networks. Popular options for data encryption software include the open-source VeraCrypt programme, the paid and open-source PGP programme, and the encryption features that come pre-installed in many operating systems and applications.
- Data Loss Prevention (DLP) tools: Tools for data loss prevention (DLP) are those that concentrate on identifying and stopping data loss or misuse. That can occur through data breaches, and unauthorized use. DLP solutions can identify and block attempts to transfer sensitive data outside authorized channels. It can transfer data by patterns such as through email attachments, USB drives, or cloud storage services. McAfee DLP, Microsoft Endpoint Data Loss Prevention, and Forcepoint DLP are some popular examples
#4 Cybersecurity Tools: Identity & Access Management (IAM):
- Multi-factor authentication (MFA):These tools provide not a single but multi layered account login procedure. This process adds an extra layer of security beyond traditional passwords. For example, along with the password, users might be asked to enter a code sent to their email, answer a secret question, or scan a fingerprint. Substitute form of authentication can help prevent unauthorized account access if a system password has been compromised and greatly reduces the risk.
- Single Sign-On (SSO):users access multiple applications with a single login credential. It enhances user experience, so it potentially reduces the security risks that comes with managing multiple passwords. SSO that are most famous are Microsoft Azure AD, Okta, and Auth0.
- Identity and Access Management (IAM) solutions: (IAM) is a user-identity based framework which ensures that only the right users have the appropriate access to technology resources. It enables the organizations to manage digital identities, and it also controls user access to important corporate information. Such processes centralize the user management, make access control processes optimal, and enforce security policies. SailPoint, Azure Active Directory, and Ping Identity are some examples used widely.
Read More: Top 3 Advanced Web Security Techniques for 2024
#5 Cybersecurity Tools: Security Information and Event Management (SIEM):
- SIEM cybersecurity toolsare used to aggregate logs and events from various security tools and systems within an organization. It provides a centralized platform for monitoring and analyzing potential security threats. Different events are correlated, suspicious patterns are identified, and security personnel are alerted to cater to potential threats. Splunk, LogRhythm, and ArcSight are popular examples.
Additional Cybersecurity Tools & Resources:
- Password managers: Password managers securely store and manage complex passwords for different accounts, minimizing the need to remember multiple passwords. Norton Vault, 1password, Lastpass are popular used password managers.
- Vulnerability management platforms:These cybersecurity tools provide a complete detailed view of threats. Such threats are identified across different frameworks within an organization. Thus prioritized patching and remediation efforts are made possible by this.
- Threat intelligence feeds:Threat intelligence is analysed dataset that is collected, processed, and analysed to understand a threat attacker’s motives, targets, and attack behaviours. It makes faster, better, informed, data-backed security decisions. The behaviour is changed from reactive to proactive against hackers.
Choosing the Right Cybersecurity Tools:
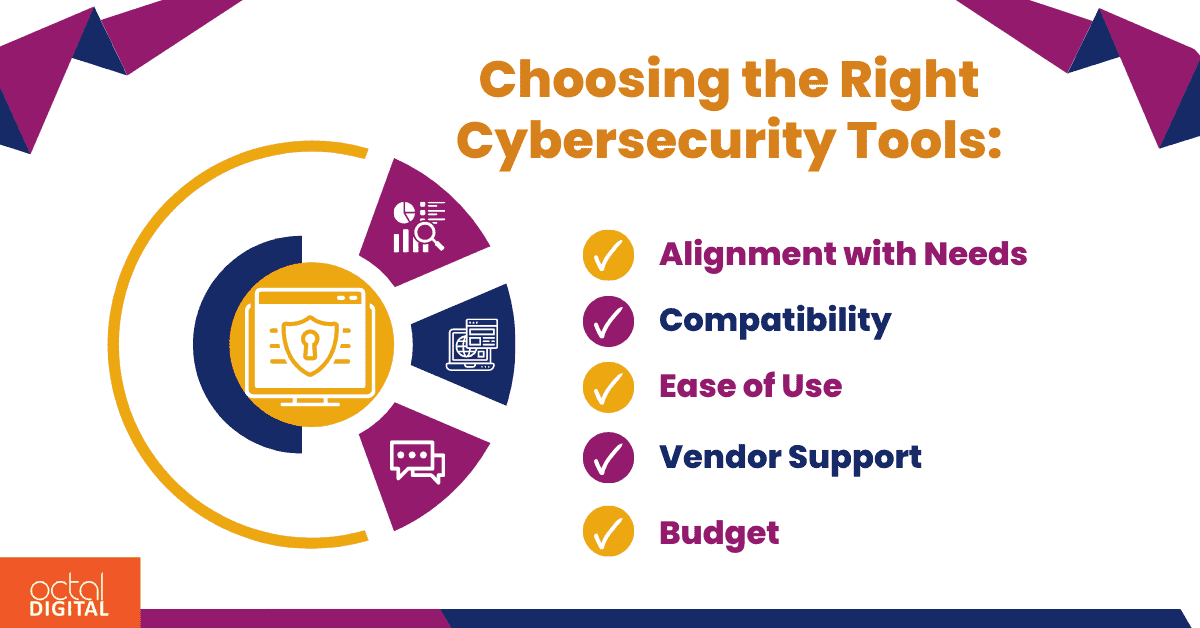
To select right cybersecurity tool for defence strategies, here are some key factors to consider when making your choices:
- Alignment with Needs: You should ensure that the chosen tools fulfill your cybersecurity needs and threats.
- Compatibility:Make sure that the compatibility of cybersecurity tools stays with the existing state of affairs in the organization. The systems such as including operating systems, hardware, and software applications.
- Vendor Support:Level of support is offered by the vendor that remains the same throughout the process. It includes training of the staff, maintenance of the system, and technical assistance from their side.
- Budget: You should choose tools that fit your budget. You should always make decisions considering ROI and conduct cost benefit analysis before that.
We understand your specific cybersecurity needs at Octal Digital, our web app solutions are curated specific to your needs. We conduct a complete assessment on the existing systems. The next step is identifying the threats, and devising a tailored strategy to address that. From strong firewalls and interference in detection systems to advanced encryption systems. By using multi-factor authentication, we use industry-leading technologies to fortify your defences. Partner with Octal Digital today make your business’s future safeguard.
Conclusion:
Cybersecurity enhancement is a crucial part in making your security system robust and increase the uptime of your services. Following best practices in cybersecurity are crucial components in maintaining best cybersecurity systems. Consider seeking professional guidance from cybersecurity experts from Octal Digital if you are stuck in assessing your needs and choosing the right tools for your specific situation.
What are some essential cybersecurity tools and software to safeguard against emerging threats in 2024?
A: In 2024, here are some advanced cybersecurity tools and softwares:
Next-generation firewalls
Endpoint detection and response (EDR) solutions
Threat intelligence platforms
Security information and event management (SIEM)
How do these cybersecurity tools differ from traditional security measures?
A: Traditional security measures depend on signature-based and perimeter detection and defenses. Modern cybersecurity tools use machine learning. To detect and respond to sophisticated cyber threats in real-time, Behavioural analysis, and threat intelligence integration are employed.
How do these cybersecurity tools differ from traditional security measures?
A: Traditional security measures depend on signature-based and perimeter detection and defenses. Modern cybersecurity tools use machine learning. To detect and respond to sophisticated cyber threats in real-time, Behavioural analysis, and threat intelligence integration are employed.
Which industries and sectors can benefit the most from leveraging these cybersecurity tools and software?
A: Every industry such as financial, government and healthcare etc. is particularly vulnerable to threats. They should employ cybersecurity because they are more prone to threats.